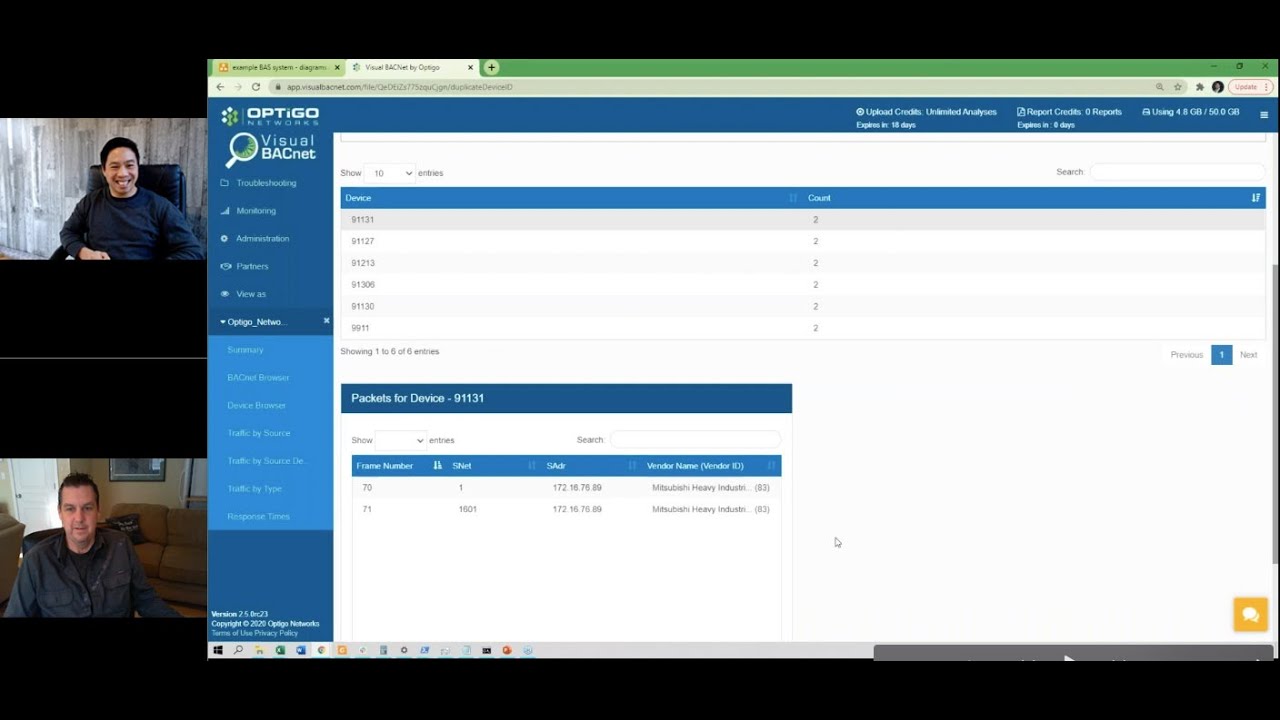
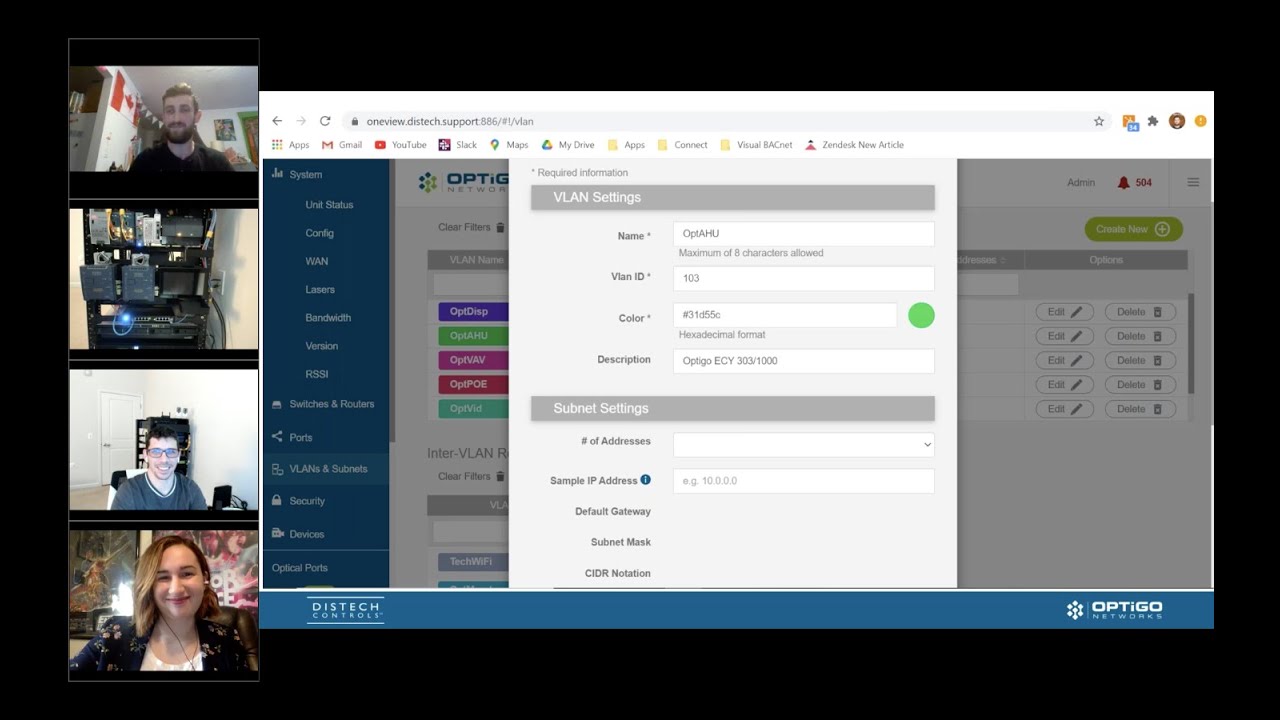
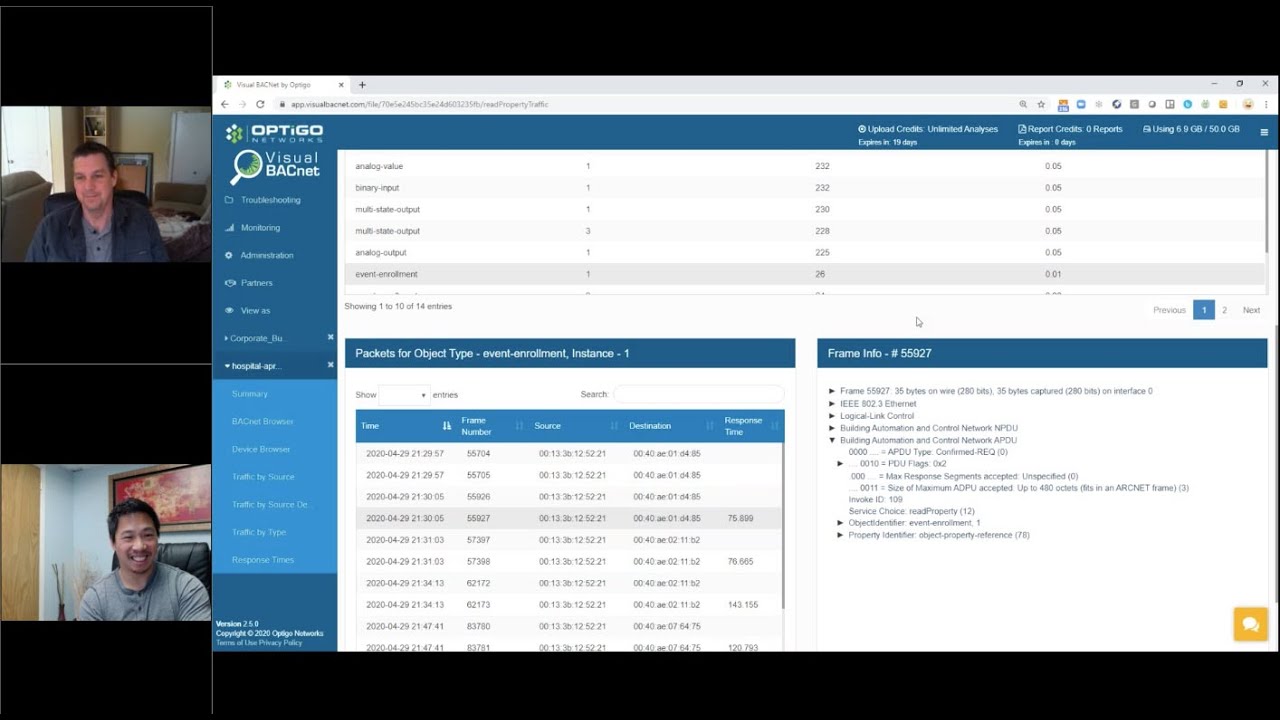
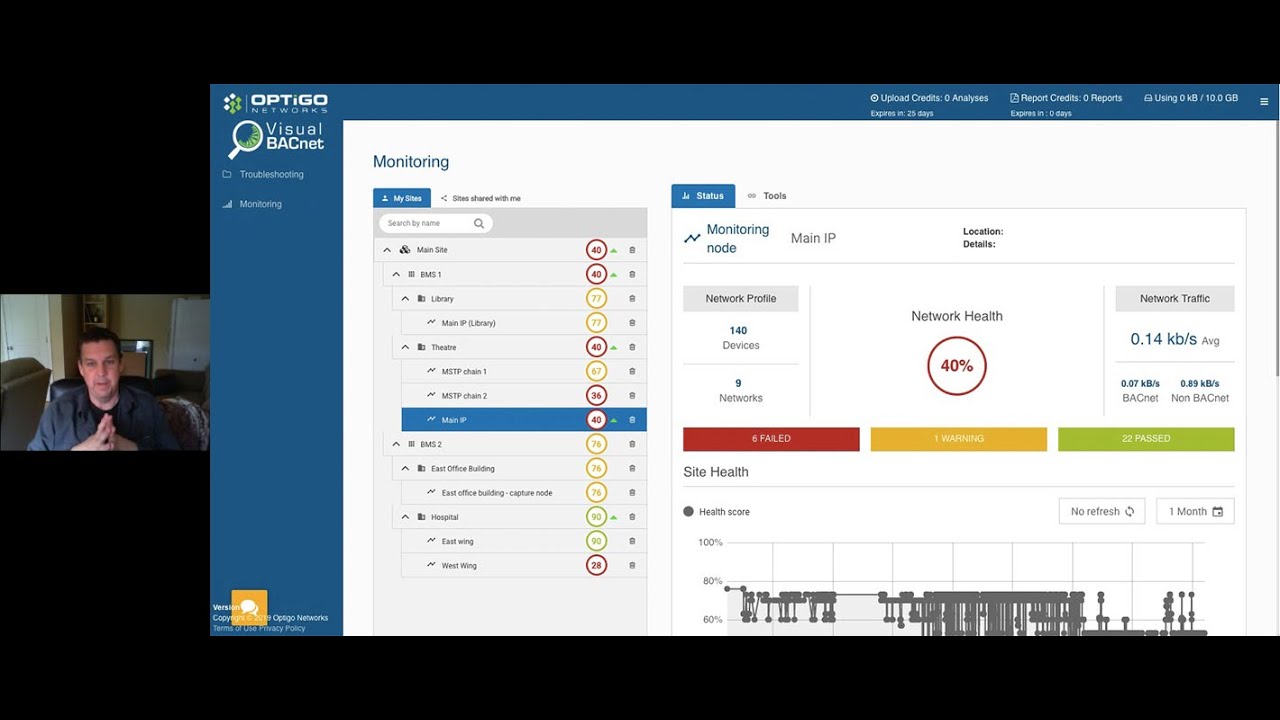
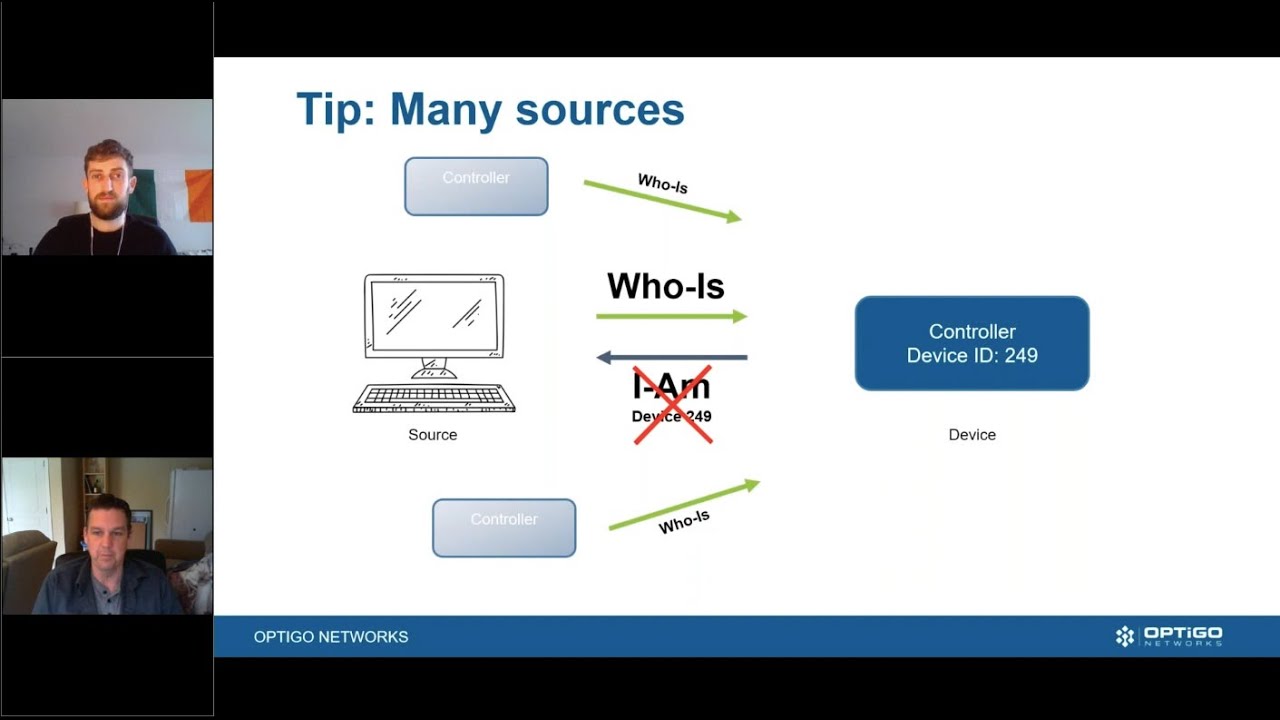
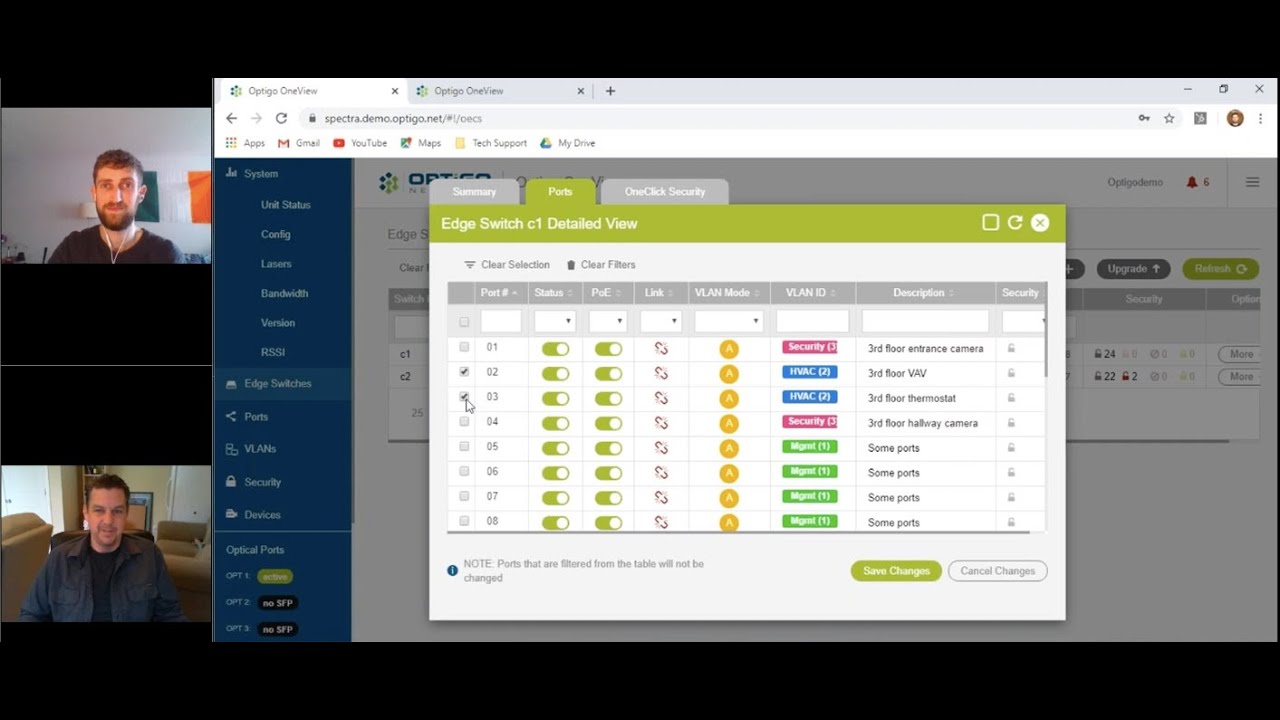
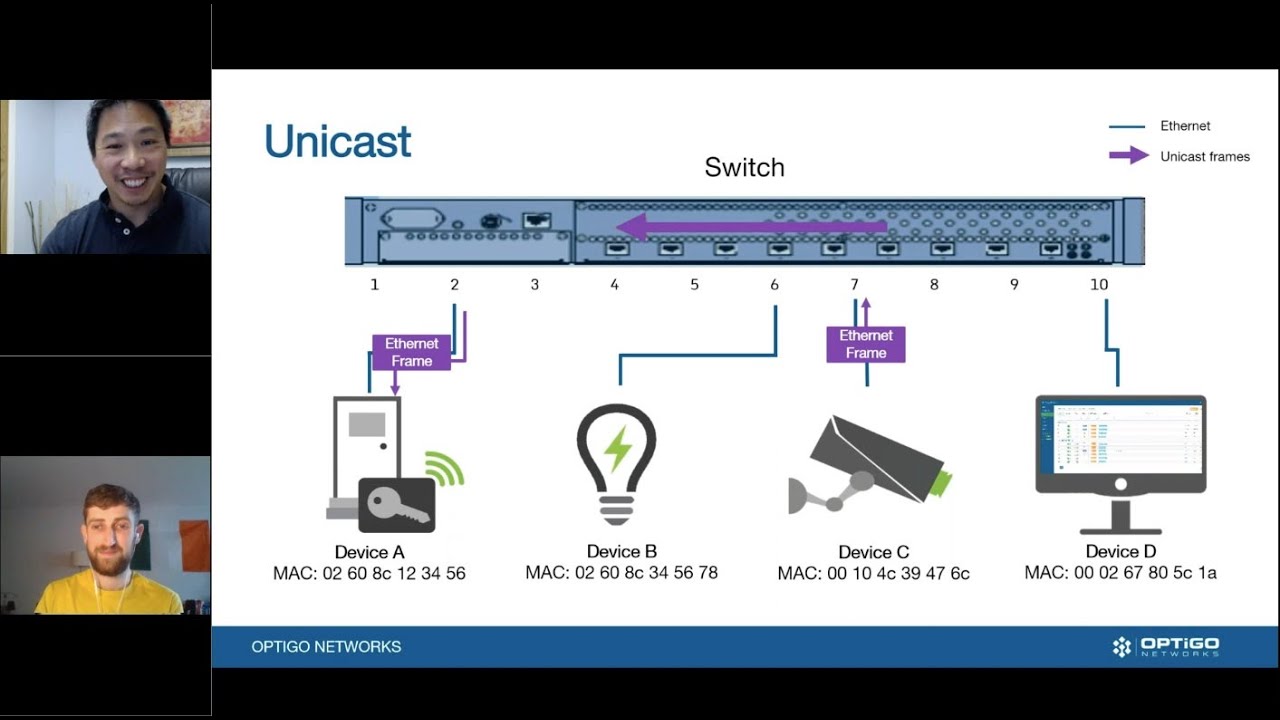
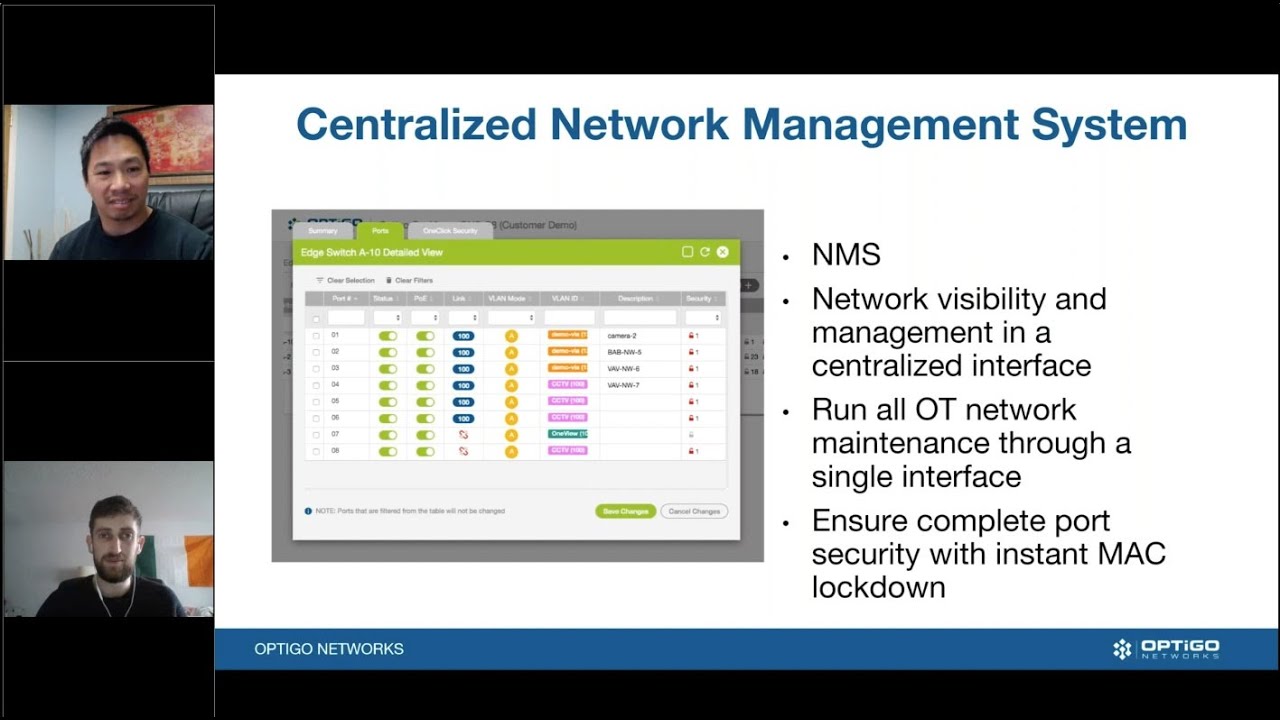
BACnet systems are shockingly vulnerable. Are your systems secure? Join us as we discuss the role of Cybersecurity in BACnet. We will consider a few hazards and consequences posed by networked BMS technology, and the legacy risks that accompany each BACnet system. You will learn how actual system commissioning or maintenance may even fail to deliver elementary security (like avoiding trivial passwords), that was assumed in the risk assessment, and how BACnet allows transmission across networks that are only partially ‘trusted’. Discover and identify the loss of service building occupants can survive, how current functionality is determined, and how you can better configure your network to withstand these risks.
CYBERSECURITY IN BACNET
KEEPING YOUR BACNET SYSTEM SAFE