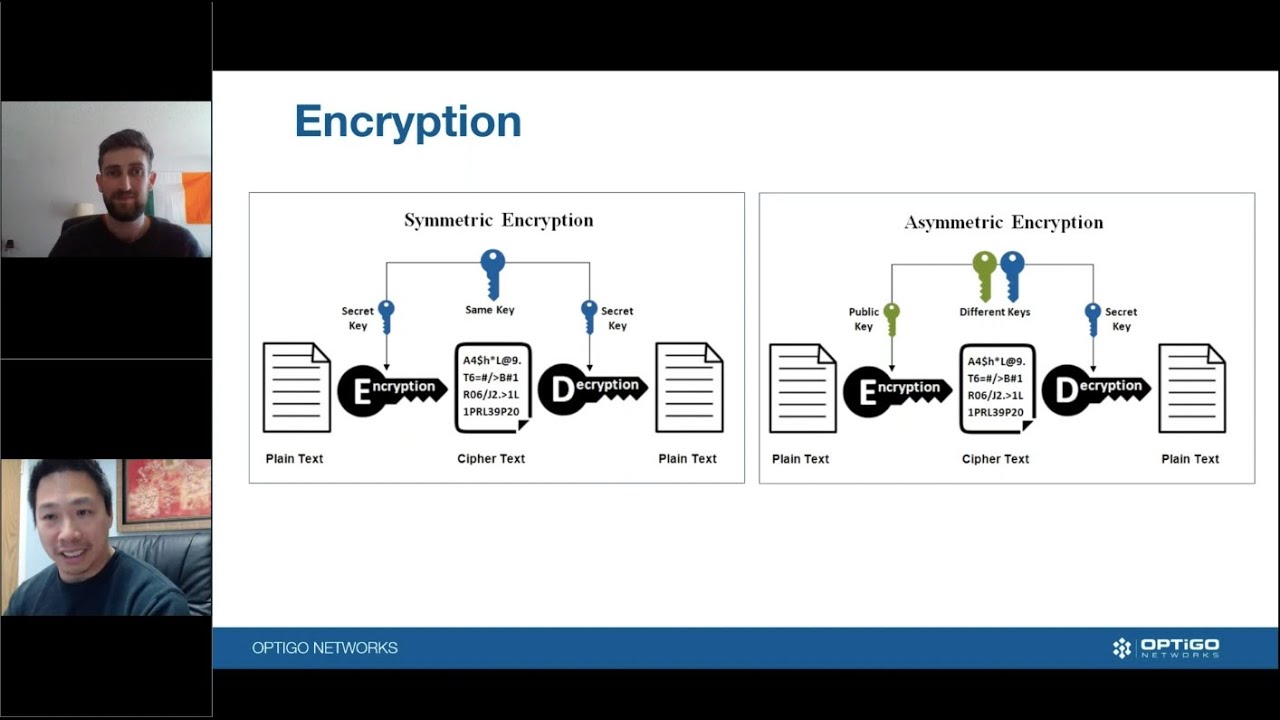
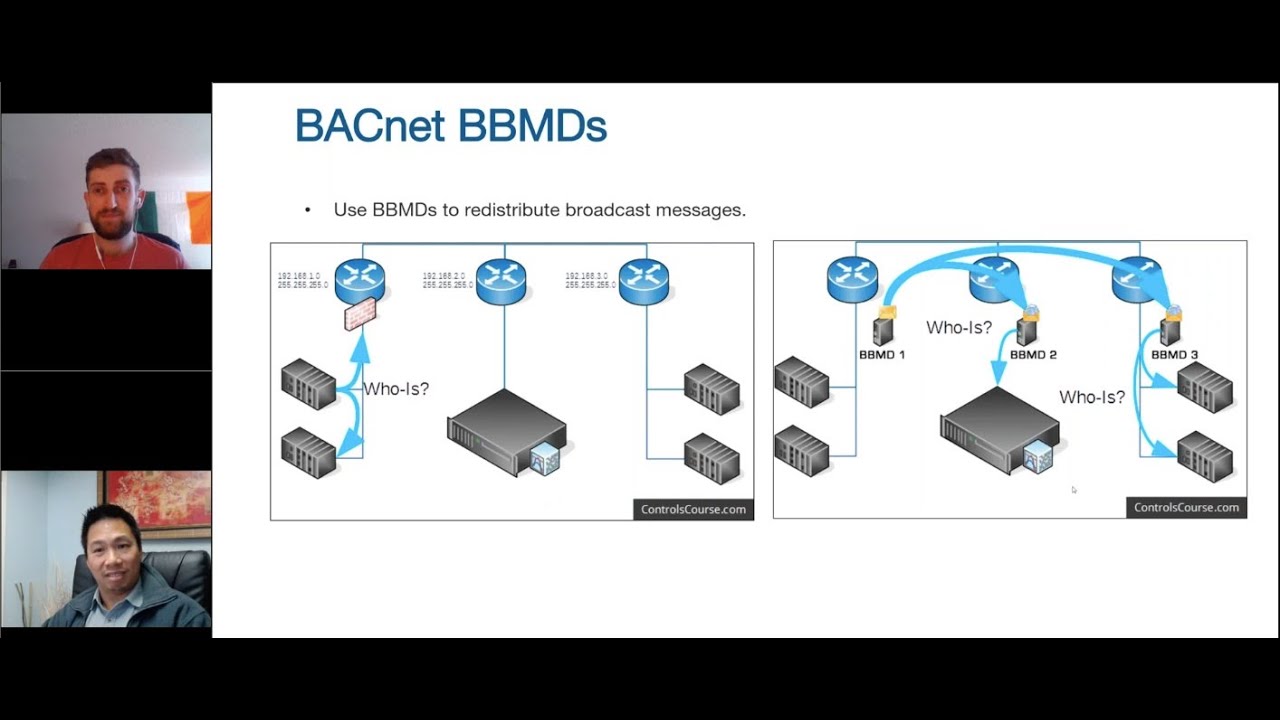
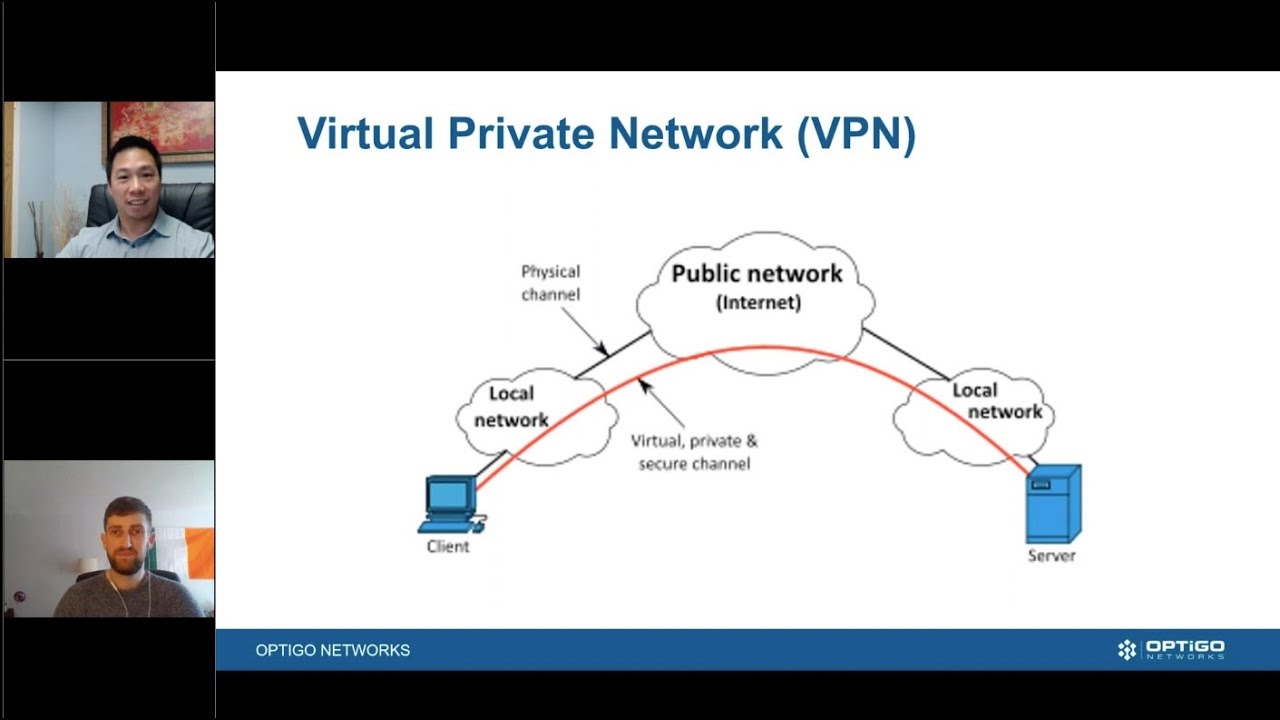
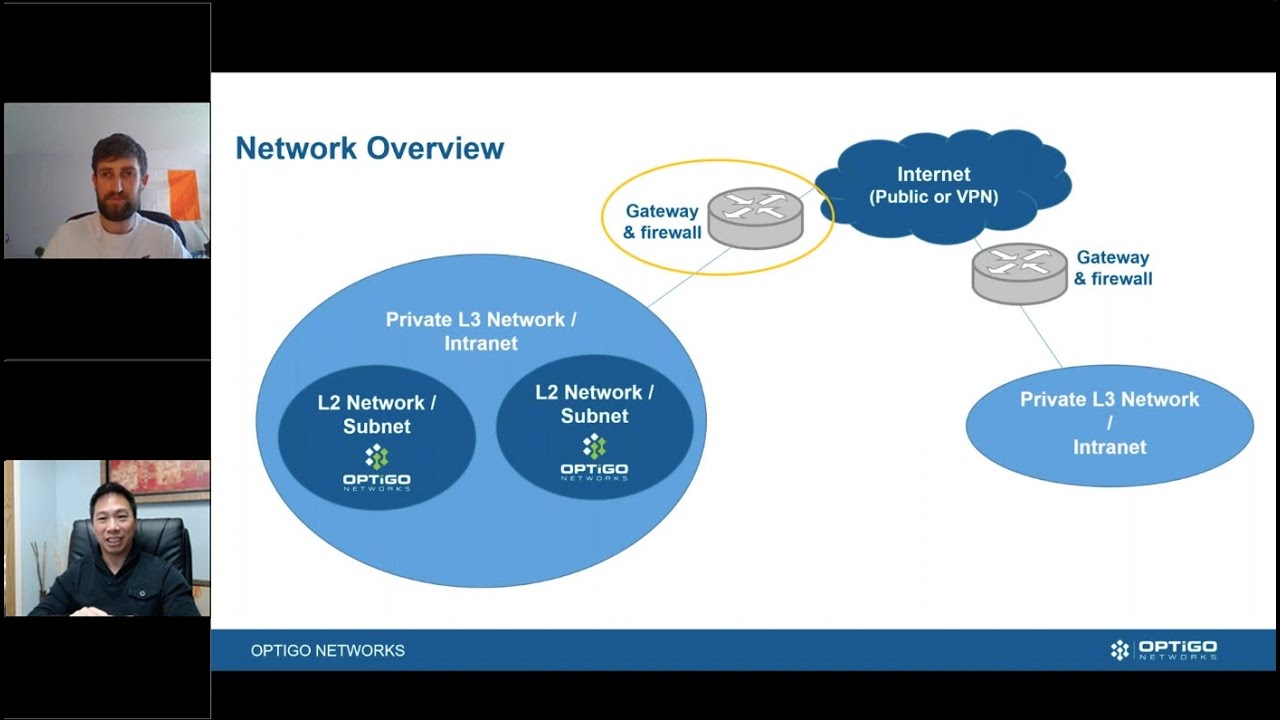
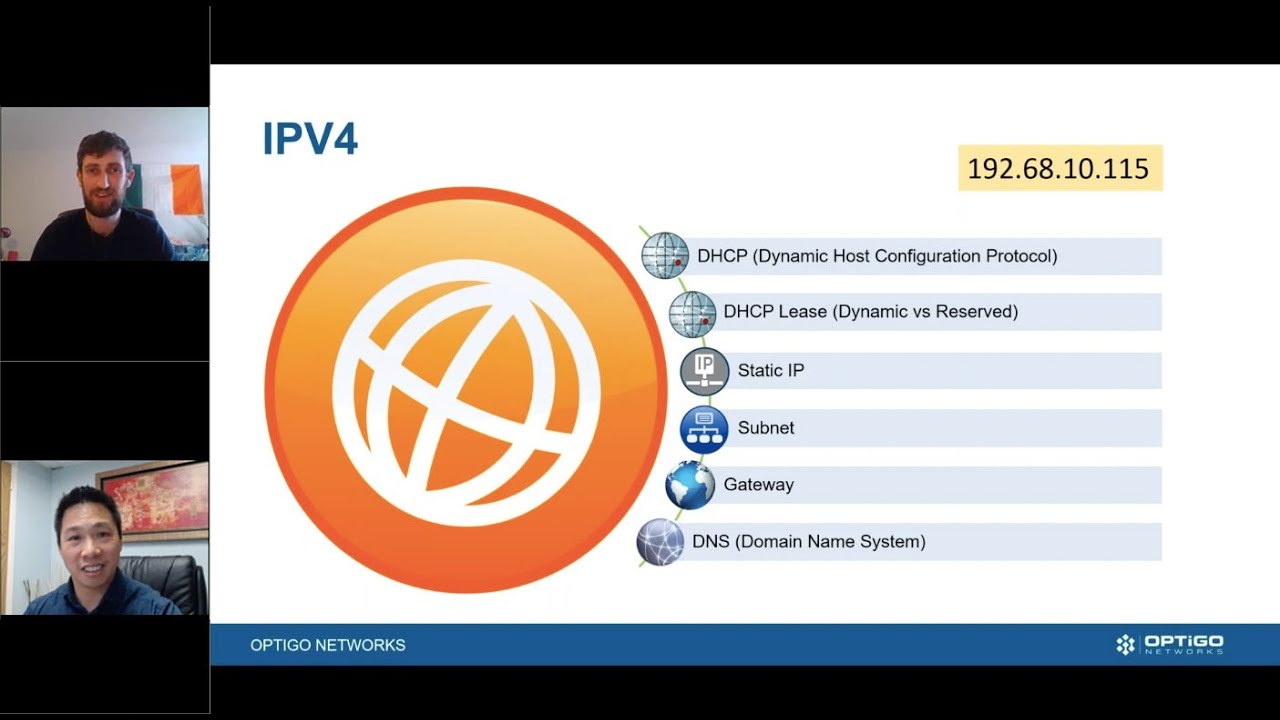
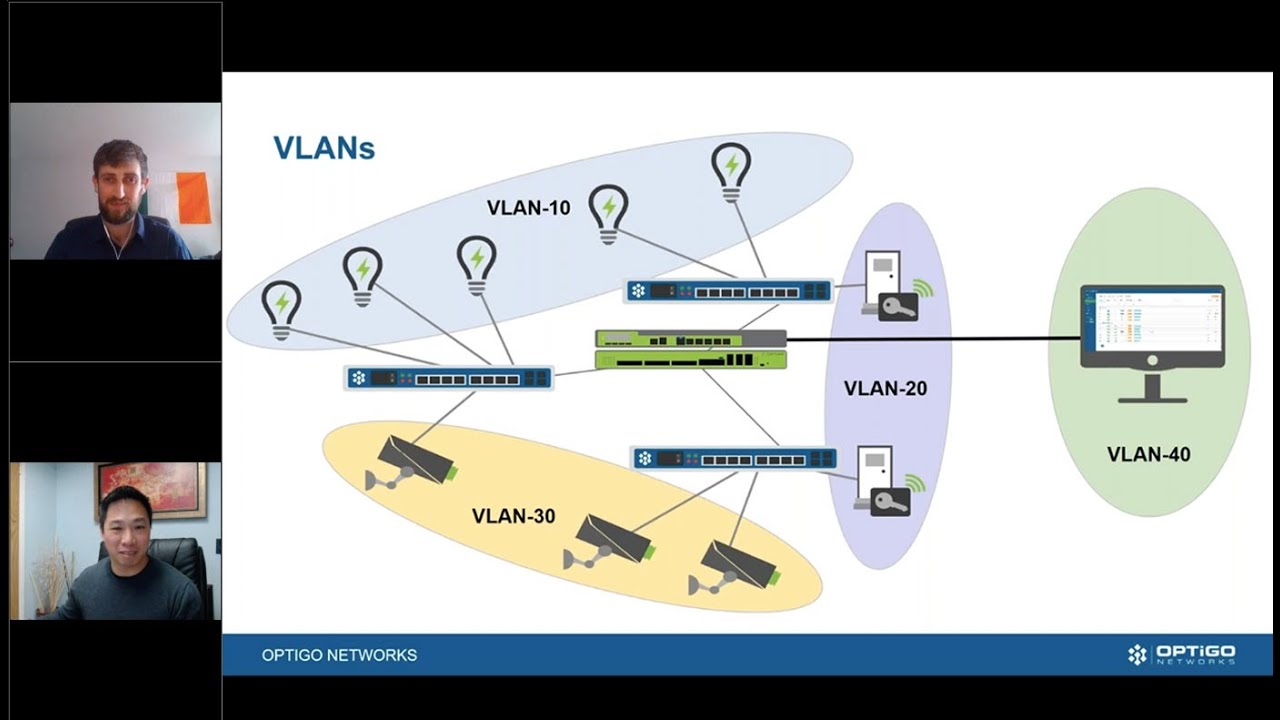
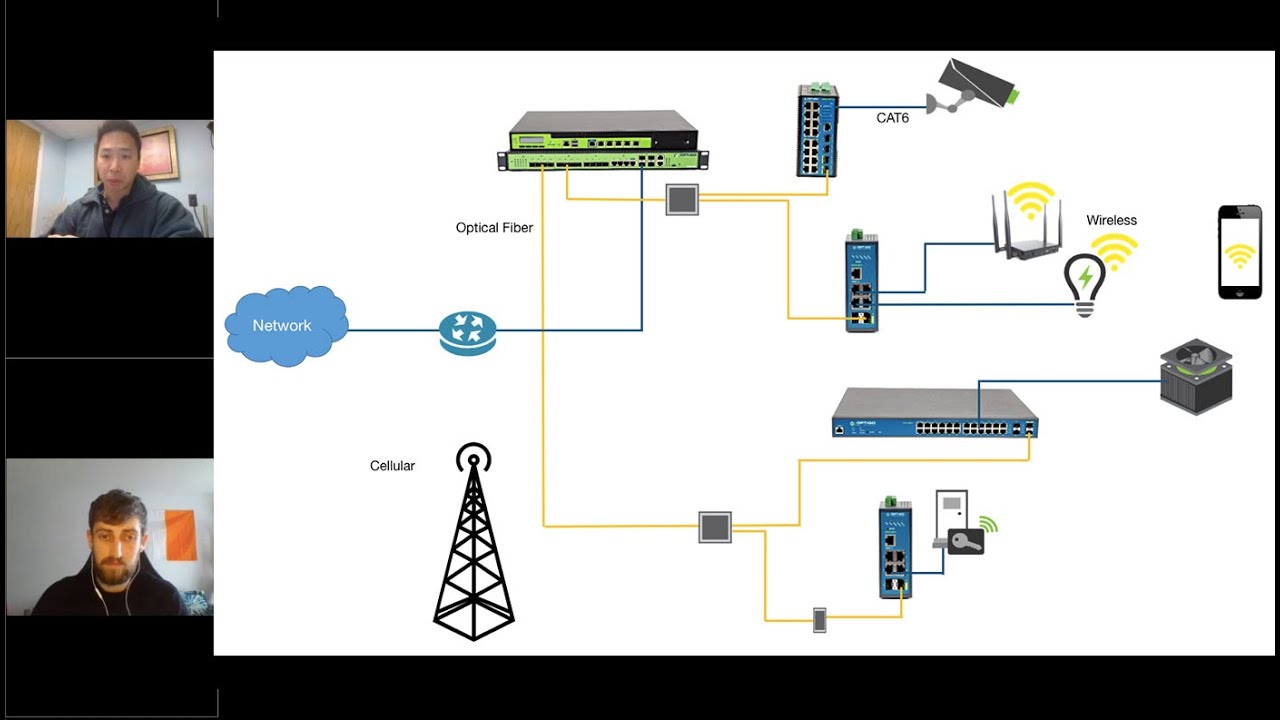
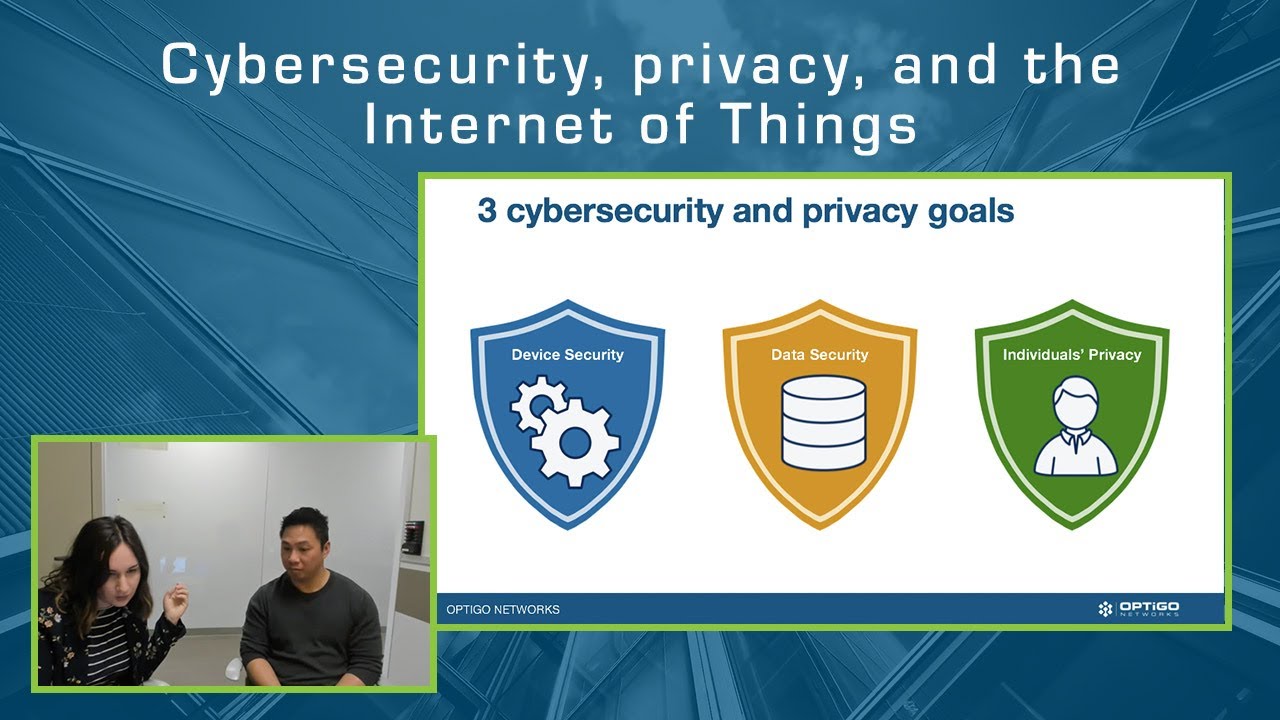
Everyone is growing more aware of the need for cybersecurity. There have been so many cyberattacks in recent years, it’s almost impossible to ignore. But there’s long been a view that cybersecurity is only an IT issue. Historically, building automation with BACnet has taken a different approach to cybersecurity, leading to confusion.
That’s changing in a big way with BACnet Secure Connect (BACnet/SC). This new technology will help keep your networks secure going forward, with new best practices that are IT-friendly and still backwards compatible with existing BACnet systems. But what does it all mean, and what do you need to know?
Join us to learn more about how BACnet Secure Connect will affect you, and what else you should know about keeping your systems secure. We’ll be talking with Bernhard Isler from Siemens and David Fisher from PolarSoft, two main figures behind BACnet/SC.